The adoption of cloud computing has become synonymous with scalability, efficiency, and innovation. As organizations increasingly migrate their operations to the cloud, the need for comprehensive enterprise cloud security best practices and strategies becomes critical. In fact, Statista found many organizations are experiencing security misconfigurations on a daily basis.
In this article, we’ll explore essential enterprise cloud security best practices designed to protect sensitive data, mitigate threats, and help ensure regulatory compliance. From encryption to access management, we’ll explore how to protect data in cloud environments to help organizations protect against emerging threats.
Understanding the Shared Responsibility Model
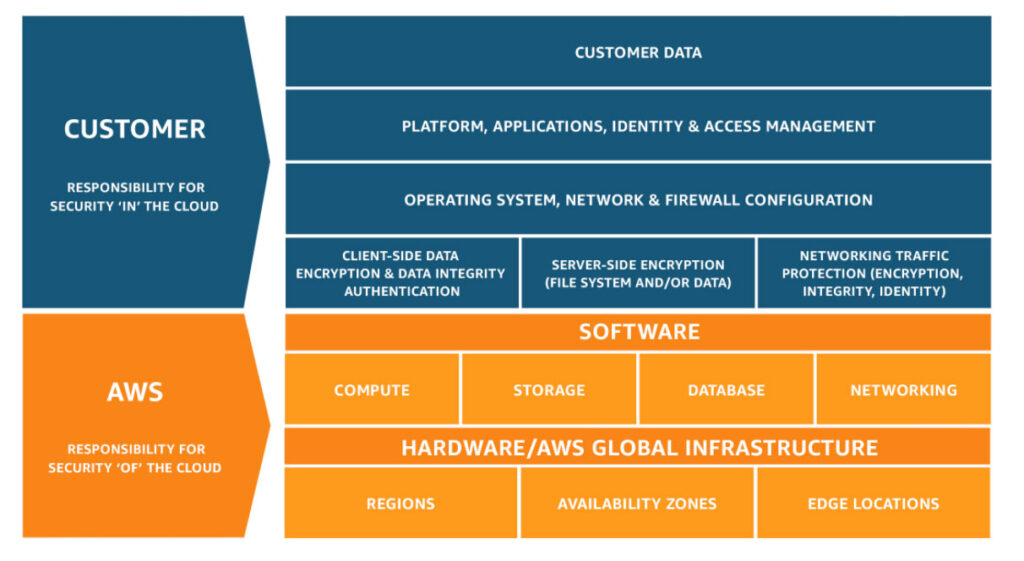
In the world of enterprise cloud security, the shared responsibility model is used as a guideline to help organizations understand what they are responsible for securing in cloud environments and what the cloud service provider (CSP) is responsible for securing.
This model helps organizations identify what needs securing if they are using cloud computing models, like Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS), or any combination of these. This understanding of responsibility is an important part of enterprise cloud security best practices.
Below is a breakdown of common models used by cloud customers and areas of responsibility for the customers and the cloud service providers (CSP).
Infrastructure as a Service (IaaS)
In IaaS, the cloud service provider (CSP) has responsibility for:
- Physical security of data centers, including access control and environmental protection
- Virtualization infrastructure, ensuring the security of hypervisors
- Network infrastructure management, including firewalls and load balancers
- Host infrastructure security, which includes protecting physical servers and host operating systems
The cloud customer is responsible for:
- Data encryption and integrity measures for data protection in the cloud
- Operating system security, including patch management and using antivirus software
- Application security, including secure code development and patch management
- Identity and access management (IAM) that governs user permissions and access controls
- Network security configurations, like firewall rules and security groups
- Configuration management, which helps ensure the proper setup and maintenance of cloud resources
Platform as a Service (PaaS)
In PaaS, the CSP is responsible for:
- Security of underlying platform components and architecture frameworks
- Maintenance of runtime environments and any associated services
- Network infrastructure management within the platform ecosystem
Cloud customers are responsible for:
- Application-level security measures, including code integrity and access controls
- Data protection in the cloud through encryption and access control mechanisms
- Identity and access management for any platform services
- Configuration management of platform-specific settings and parameters
Software as a Service (SaaS)
In SaaS, cloud service providers are responsible for:
- The overall security of the SaaS application, including access controls and authentication mechanisms
- Data protection within the cloud SaaS platform, including encryption and compliance measures
Cloud customers are responsible for:
- User access management and permissions within the SaaS application
- Data protection strategies that are tailored to the specific requirements of the organization
- Integration of the SaaS application with existing security frameworks and protocols across the organization
A Real-life Example of Shared Responsibility
If an organization wants to secure an Amazon Elastic Compute Cloud (EC2) instance, then the responsibility for security would be split between the cloud service provider (CSP) and cloud customer as follows.
The cloud service provider (CSP) in this example is Amazon AWS and their security responsibility would include ensuring the physical security of the data center. This would include providing a secure hypervisor and managing the underlying network infrastructure.
The cloud customer’s security area of responsibility would include the following.
Data Encryption
The cloud customer is responsible for encrypting data at rest and in transit for data protection in the cloud. They can use the AWS Key Management Service (KMS) for key management and enable encryption for EBS volumes.
Operating System (OS) Security
The customer is responsible for securing the guest operating system by regularly applying security patches, configuring firewalls, and installing anti-malware software.
Application Security
If the EC2 instance hosts a web application, the customer must secure any application code, apply web application firewalls (WAFs), and protect against common web vulnerabilities.
Identity and Access Management (IAM)
Cloud customers define who or what can access the EC2 instance and what actions they can perform. One way to accomplish this in AWS is by using AWS Identity and Access Management (IAM).
Network Security
The cloud customer would be responsible for configuring security groups and network access control lists (ACLs) to control inbound and outbound network traffic to the EC2 instance.
Configuration Management
The cloud customer would be responsible for ensuring proper configuration of the EC2 instance, including disabling unnecessary services and restricting access.
The shared responsibility model helps organizations gain visibility into their enterprise cloud security and helps them build a more effective cloud security strategy. Security in cloud environments is complex and challenging for many organizations, which is why cloud service providers often provide best practices for building more securely (such as the AWS Well-Architected Framework).
Data Protection
The IBM Cost of a Data Breach Report for 2023 revealed that over 83% of data breaches involved data stored in cloud environments. To protect sensitive data in cloud environments, organizations need to implement effective enterprise cloud security strategies. The first step is identifying and classifying data, a process that is critical for customizing security measures to mitigate risks adequately.
Data classification involves categorizing data based on sensitivity and regulatory requirements. It involves four main types of data: Public Data, Internal Data, Confidential Data, and Highly Confidential Data. Each category demands different levels of security controls, from minimum for public data to strict security controls for highly confidential data.
Regulatory requirements such as PCI DSS, HIPAA, and GDPR impact data classification by mandating organizations to classify data according to sensitivity and implement appropriate security controls.
In cloud environments, organizations can leverage various tools and techniques for data protection including data encryption, access control, data loss prevention (DLP), and data backups.
Implementing these tools and techniques helps organizations secure their cloud environments against data breaches and ensure compliance with regulatory requirements.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is an important part of enterprise cloud security strategy. IAM includes the technology, processes, and policies governing digital identities within organizations’ cloud environments. It facilitates appropriate access to information while preventing unauthorized entry.
IAM offers granular access control, helps organizations ensure compliance with regulations, and helps protect against insider threats. By defining specific access policies, organizations ensure users, applications, and systems access only necessary resources. For example, healthcare organizations can restrict patient data access through IAM, helping them comply with regulations like HIPAA.
IAM helps streamline security compliance by implementing and automating security controls, auditing access, and maintaining an audit trail. It mitigates insider threats by detecting and preventing unauthorized access and misuse.
IAM’s centralized management simplifies identity administration across cloud environments. Some IAM best practices include multi-factor authentication (MFA), least privilege, Role-Based Access Control (RBAC), access logging, and identity federation.
For example, in AWS, a financial institution can enforce MFA for IAM users, restrict permissions, define roles, monitor with CloudTrail, and enable federation for seamless access.
Overall, IAM is a cloud security best practice that helps protect critical data and services, but effective cloud security begins with comprehensive governance.
Cloud Security Governance
Cloud security governance includes the policies, processes, and controls that govern an organization’s use of cloud services to help ensure security and ensure that the organization’s business objectives can be accomplished.
It defines the security standards, procedures, and guidelines to reduce risks associated with cloud adoption, while ensuring compliance with regulatory requirements and industry standards. Cloud security governance is really just a structured approach to managing enterprise cloud security.
For effective enterprise cloud security, cloud security governance offers a centralized framework for managing cloud risk, helps ensure regulatory compliance, and helps organizations optimize resource use.
Let’s look at an example of applying cloud security governance to a healthcare organization.
First, the healthcare organization needs to identify regulations and standards that it needs to be in compliance with. One example is the Health Insurance Portability and Accountability Act (HIPAA).
To comply with HIPAA, the organization would craft a security policy that outlines responsibilities for secure data handling, encryption protocols, and regular audits of the cloud infrastructure to ensure patient data is protected.
The organization would also provide training to its employees on HIPAA and requirements for secure data handling.
The organization should also develop a detailed incident response (IR) plan that is aligned with HIPAA breach notification requirements and conduct regular tabletop exercises to validate the effectiveness of the IR plan.
In AWS, a few tools that can help organizations with compliance requirements include AWS Artifact which helps them download compliance reports and certifications, and AWS Config which helps them audit for compliance against regulatory requirements.
By embracing effective governance practices, organizations can mitigate security threats and unlock the value of leveraging the public cloud, while ensuring data protection in the cloud.
Security Auditing and Assessment
Security auditing and assessment includes the systematic examination and evaluation of an organization’s cloud infrastructure, policies, and controls to identify vulnerabilities, assess their security posture, and mitigate risks. It involves a breadth of activities, including vulnerability assessments, penetration testing, compliance audits, and security reviews.
Security auditing can help organizations with enterprise cloud security in multiple ways, including:
Risk Identification and Mitigation
Security auditing and assessments enable enterprises to proactively identify and mitigate security risks within their cloud environments. By conducting comprehensive assessments, organizations can uncover vulnerabilities, misconfigurations, and potential attack vectors, allowing them to implement security controls to strengthen their security posture.
Compliance
Security auditing and assessments help organizations ensure compliance with regulatory requirements, like GDPR, HIPAA, PCI DSS, and SOC 2. By conducting regular audits and assessments, organizations can show their compliance, mitigate any regulatory risks, and ensure the trust of customers and other stakeholders.
One thing to note is that while many cloud service providers (CSP) are compliant with regulations, they will often just provide a certification of the compliance and not provide organizations with detailed assessments from the certification process. This is because the CSP does not want to reveal sensitive internal information in the compliance report.
Continuous Improvement
By regularly evaluating security controls, monitoring for emerging threats, and adapting to new cloud security best practices, organizations can improve their resilience to cyber threats and stay ahead of emerging threats.
Third-Party Validation
Security auditing and assessment provide third-party validation of an organization’s security posture, which can help in obtaining cyber insurance and in offering assurance to key stakeholders. Engaging external auditors to conduct independent assessments, enterprises can validate the effectiveness of security controls, demonstrate due diligence, and build trust with stakeholders.
Incident Response
Security auditing and assessment can also help organizations prepare for and respond to security incidents more by identifying and mitigating vulnerabilities before they are exploited by threat actors. This helps organizations reduce their attack surface area and improve overall enterprise cloud security.
Security audits and assessments are an important part of effective enterprise cloud security because they help organizations ensure compliance and take a more proactive approach to improving their security posture.
Amazon AWS and other cloud service providers offer tools that can help with security auditing, monitoring, and audit trails. For example, AWS CloudTrail can help organizations log API calls and user activity to detect anomalies.
Security Automation and Orchestration
Effective enterprise cloud security requires agility and scalability, which is achievable through Security Orchestration, Automation, and Response (SOAR). Security automation streamlines repetitive tasks, while orchestration coordinates diverse security tools and processes, facilitating rapid threat detection and response.
SOAR enhances efficiency and scalability by automating workflows like vulnerability scanning and compliance checks, aligning with cloud infrastructure growth. Automated security policies ensure compliance with regulatory standards, which helps reduce the risk of penalties.
Proactively, automation also aids in threat hunting and intelligence gathering, which is critical for identifying emerging threats faster. Other strategies, like leveraging Infrastructure as Code (IaC), enable consistent and secure cloud deployments. For instance, AWS CloudFormation templates ensure uniform infrastructure configurations across the enterprise.
Cloud security orchestration automates incident response, integrating with cloud providers, like AWS, and SIEM solutions for threat mitigation. DevSecOps integration embeds security practices in the development lifecycle, detecting vulnerabilities early. Automated security scanning in CI/CD pipelines ensures secure code deployment.
For example, a SaaS provider hosting sensitive data on AWS could utilize IaC for consistent deployments, cloud security orchestration for automated incident response, and DevSecOps integration for early vulnerability detection in their software development. These practices can help improve overall enterprise cloud security.
Enterprise Cloud Security Best Practices: Conclusion
As you can see, enterprise cloud security best practices are complex and require strategic planning and implementation across multiple teams. This is why organizations need skilled cybersecurity professionals to help them navigate this complexity.
Flatiron School can assist you with building cybersecurity skills to help organizations protect their cloud environments through our Cybersecurity Bootcamp program – apply today to get started towards a career in Cybersecurity!