Phishing attacks can take many forms, none of them savory. October is Cybersecurity Awareness Month, and Flatiron School has compiled a collection of tips that you can use to protect your devices and sensitive personal information.
Phishing attacks are a type of social engineering—malicious activities that are conducted through human interaction—used to steal users’ sensitive personal information for illicit gain and manipulation. An attacker approaches a user, typically through email or text message, to attempt to trick them into opening a link that leads to malware or dupe them into divulging information such as their social security number, banking information, or passwords.
Even the most vigilant email users can fall victim to phishing attempts, but watching out for these red flags can keep you from getting hooked.
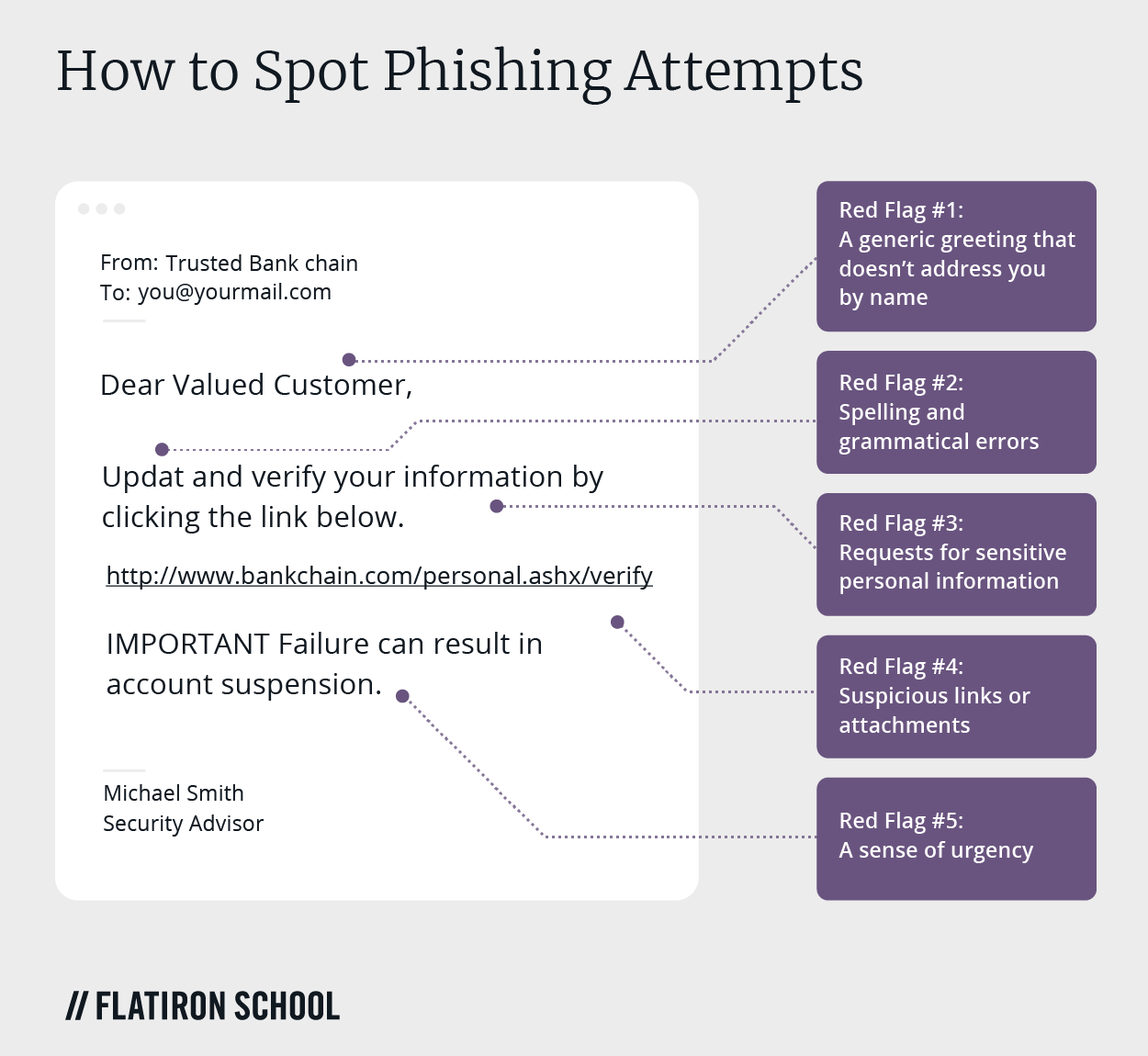
Red Flag #1: A generic greeting that doesn’t address you by name
Legitimate companies that you do business with, like a bank, social media site, or wireless service, would almost assuredly call you by name in the opening greeting of the communication. Phishing emails often start with something generic such as “Dear Valued Customer,” or “Dear Sir or Madam,” instead of your real name. Unspecific phrases such as these should signal you to send the shady email right to your trash folder.
Red Flag #2: Spelling and grammatical errors
A poorly written email splattered with spelling and grammatical mistakes is another red flag to be on the lookout for when you receive a questionable email or text message. A legitimate organization would not circulate any sort of unprofessional message to members or customers. The occasional typo might make it into an authentic communication, but generally speaking, a reputable company has professional writers and editors composing and proofreading each message.
Red Flag #3: Requests for sensitive personal information
It’s more likely than not that if you receive an unsolicited email from an institution claiming to be a bank or credit card company and telling you to click a link to provide sensitive personal information, it’s a phishing attempt. Legitimate institutions won’t send you links requesting you to log in or enter any personal details.
Don’t click the link, either, even just to check it out. Some phishing attempts like this can infect your computer with malware as soon as you open the link.
Red Flag #4: Suspicious links or attachments
The same goes for the internet, which is riddled with suspicious links and attachments. The text of a link can be anything at all, and just because it says something like Secure Link, doesn’t mean it is. (This one’s safe though, and only leads to further information about phishing and defending yourself from attempts on your personal data.)
The attachment may contain a malicious URL or Trojan, which can install viruses and malware. Sketchy attachments with filenames ending in something other than .doc or .PDF, such as .EXE, will begin running the instant you click them. A good rule of thumb is to have your antivirus software set up to automatically scan all incoming attachments before allowing you to open them. This protects you from even the most authentic-seeming attacks.
Red Flag #5: A sense of urgency
A common ploy among phishing attacks is that they are designed to instill a sense of urgency. The attackers attempt to panic you into an emotional state that makes you more likely to click links and attachments. Defuse the panic by letting your cybersecurity awareness take over.
The email might say things such as your credit card information has been compromised, you need to act immediately to avoid account closure, or you must pay a utility bill before the lights are turned off. Be wary with all emails, and take the time to think about whether the sender is asking for reasonable information. A legitimate institution will never ask for your passwords, social security number, bank account number, or other sensitive details.
How to report attempted phishing attacks
If you receive an email or text message that you suspect might be—or clearly is—a phishing attack, there are a number of steps you can take to report the incident. The information you share will be used to help fight scammers and better secure the networks you use.
-
Flag the email as spam in your email client or under message options on your mobile phone. If your company has an internal network, you can also notify the IT administrator.
-
If the phishing attempt was made through email, you can forward it to the Anti-Phishing Working Group at reportphishing@apwg.org.
-
Phishing attempts made via text message can be forwarded to SPAM (7726).
-
You can also report the phishing attack to the Federal Trade Commission.
When in doubt, throw it out
If you’re in doubt about the legitimacy of links or attachments in emails, texts, social media posts, or online advertisements, don’t click them. Better yet, delete questionable emails and texts immediately so you don’t accidentally open harmful malware.
If you’d like to continue learning about how you can prevent phishing attacks, try Flatiron School’s free online lesson covering different phishing techniques and how companies can combat them.




