Cybersecurity is quite the trending topic lately. While it’s certainly been in the news more and more often recently – affecting individuals, companies, and even entire countries – in reality, data vulnerability has been a tremendous concern for a long time.
At the forefront of these efforts are those people in the cyber weeds, working to ward off cyber threats and vulnerabilities. These are the SOC teams, analysts, responders, and — perhaps most of all — cybersecurity engineers.
In this blog, we’ll cover what a cybersecurity engineer does, how to become a cybersecurity engineer, cybersecurity engineer skills, and the potential paths one may take to become one.
What does a cybersecurity engineer do?
While a vitally important role within any organization, it can oftentimes be unclear for the uninitiated to answer the simple question “what does a cybersecurity engineer do?” The title of cybersecurity engineer — sometimes called an information security engineer, data security engineer, or web security engineer — is someone who comes up with ways to protect devices, services, and networks from malicious digital attacks. A cybersecurity engineer also designs and implements secure networks and ensures that the network and its attendant resources (databases, printers, smartphones, etc.) are protected from cyber-attacks.
The security engineer also regularly tests and monitors the security systems to ensure they are up to date and functioning properly. Organizations and/or individuals hire these engineers to help protect organizational data, sensitive and confidential information, financial/transactional information, and the reputation of the organization as a whole. To this end, they primarily protect data from data breaches.
Responsibilities of a cybersecurity engineer
The responsibilities of a cybersecurity engineer have a lot of overlap with cybersecurity analysts, who are also tasked with protecting sensitive information. The duties of those in the role of cybersecurity engineering include:
- Planning, implementing, managing, monitoring, and upgrading security measures and infrastructure to protect organizational data and resources
- Making sure adequate security measures and protocols are in place to secure organizational data
- Troubleshooting network and security issues
- Testing and identifying network and system vulnerabilities
- Responding to security breaches with their SOC team comprised of cybersecurity analysts, pen testers, security consultants, cyber threat analysts, and sometimes compliance analysts.
- Liaising with the appropriate departments of the organization in the course of security duties
- Administrative duties and report writing
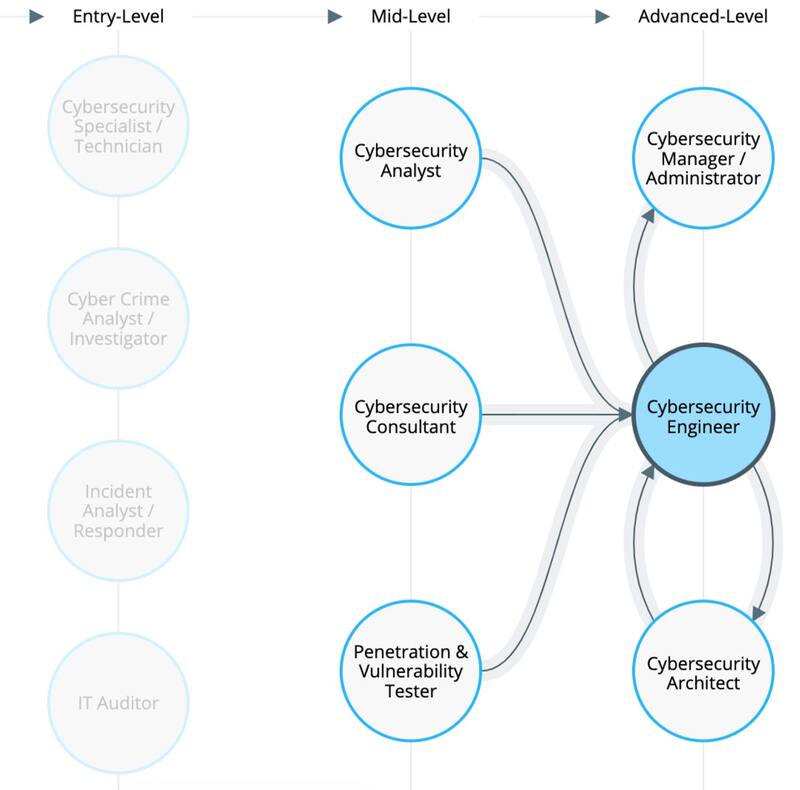
Job opportunities for a cybersecurity engineer
According to statistics from the US Bureau of Labor, job opportunities in cybersecurity are projected to grow by 32% between 2022 and 2032, with unemployment in the field is nearly zero.
These roles are going to be right in line for people with cybersecurity engineering skills.
Cybersecurity engineers can work as network security engineers, IT security engineers, security analysts, penetration testers, information assurance engineers, and information systems security engineers, to mention a few. All of these jobs are high-paying, future-proof careers, too.
The mean salary for security analysts nationally is ~$100k. For pen testers, that number is ~120k.
Hard Skills Cybersecurity Engineers Need
Hard technical skills are a critical skill set for cybersecurity engineers to have. Whereas analysts require slightly less technical expertise, engineers are valued for their hard skills. These skills are a requirement for anyone looking to enter and succeed in the cybersecurity space — and especially engineers.
Programming Langauges:
Proficiency in cyber programming languages like C/C++, Java, Python, Go, and Ruby, is a huge advantage. Each has its own use case.
Python
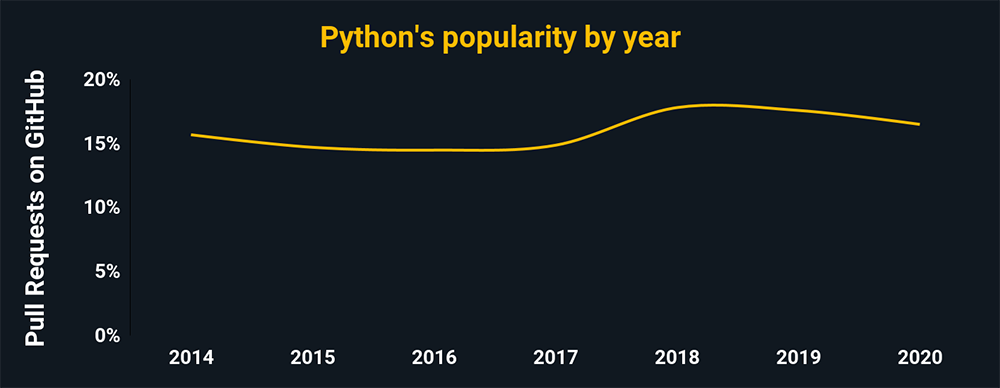
- Python’s used to automate tasks and malware analyses
- It can also be used in pen testing and scanning
- Python’s a general-purpose language used in most cybersecurity situations
- Python’s also easier to learn than most other cyber coding languages
The charts above and below show the relative popularity based on how many GitHub pulls are made per year for that language. They are based on data from GitHut 2.0, created by littleark.
C/C++
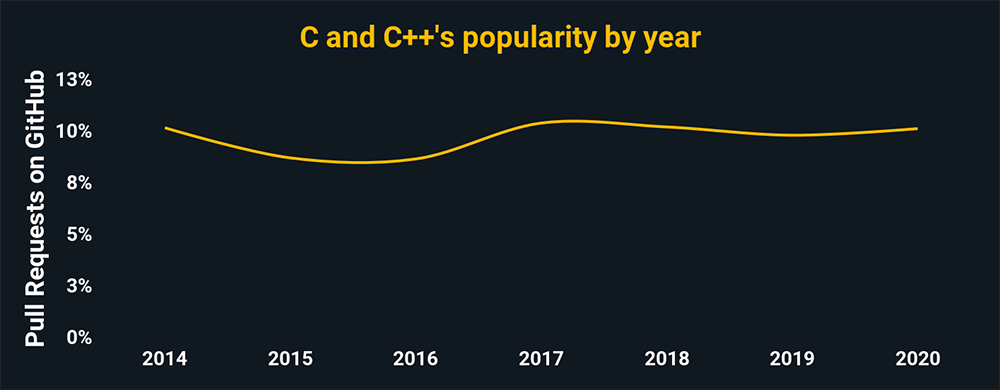
- C in reverse engineering helps develop antivirus programs because a cyber team can dissect and diagnose malware
- C is essential for QA’ing code integrity
- C can be used for secure network solutions
Java
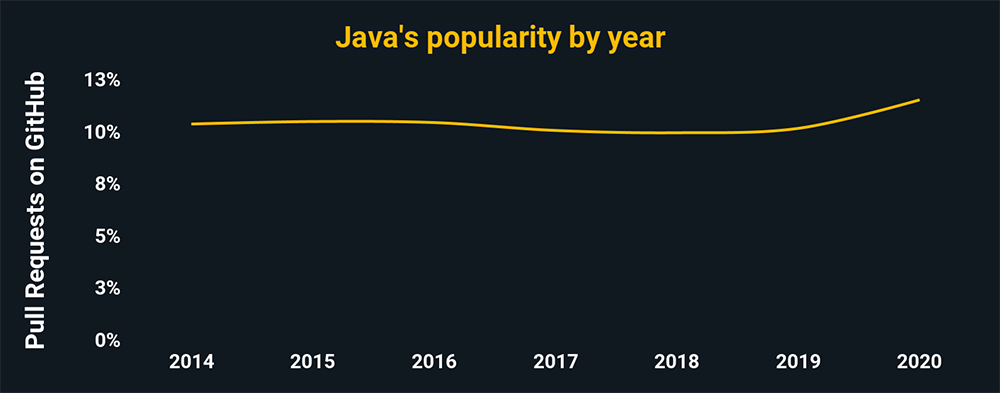
- Bad actors use Java to reverse-engineer proprietary software apps and to exploit security vulnerabilities.
- Pen testers can use Java to organize high-scaling servers
- Java, just overall, is widely helpful in pen testing
- Ethical hackers use Java to build and develop sophisticated
- Java is highly dynamic compared to languages like C++, making it popular among cyber experts.
Go (Golang)
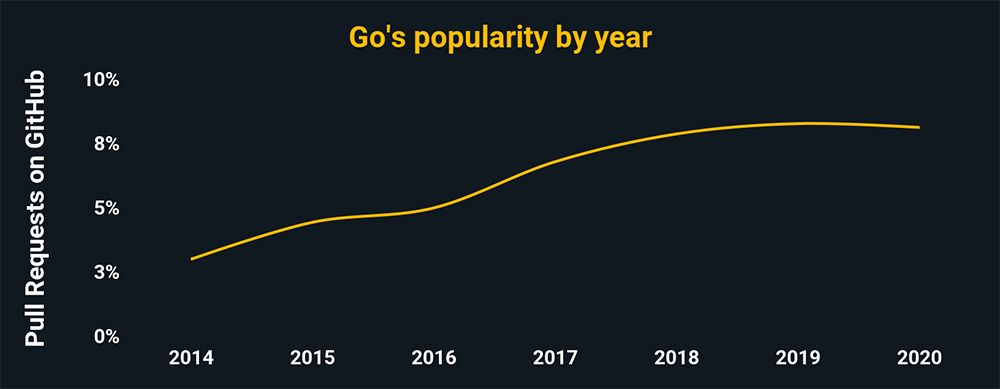
- Go is perfect for discovering malware
- Go is also simple and scalable
- It’s also popular among bad actors because Golang malware is large, making intrusion detection by antivirus software harder
- Go has extensive libraries that make malware creation easier
JavaScript
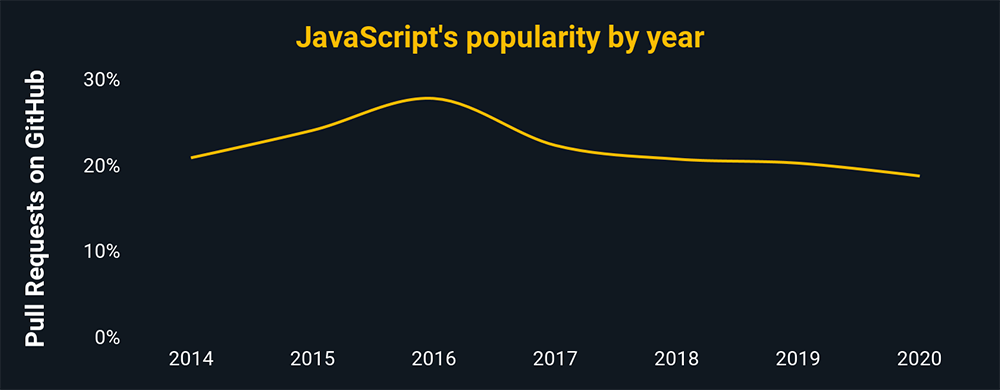
- JavaScript is useful for capturing cookies, exploiting handers, and cross-site scripting
- Node.js, React.js, jQuery are all JavaScript libraries.
- This also implies that, due to the widespread use of the language, applications and systems using it are prominent targets.
Ruby
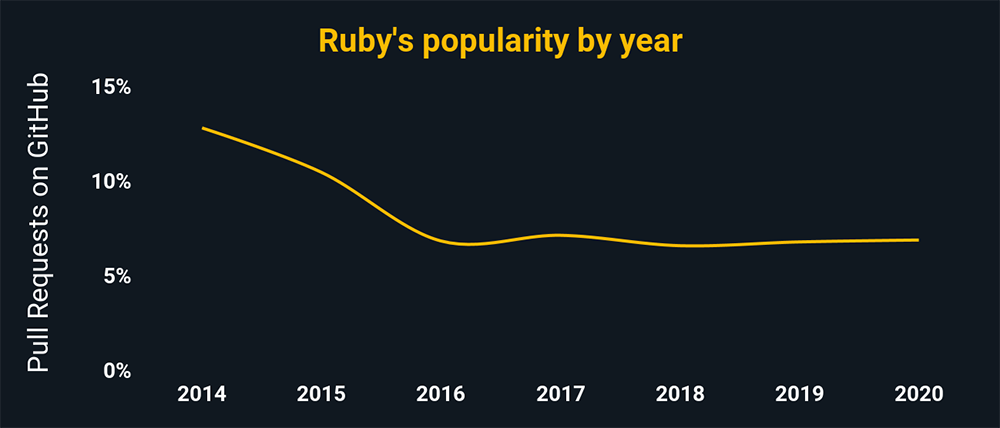
- Ruby’s syntax is essentially identical to Perl and Python and was written in C.
- It’s used to manage massive code projects, making it a popular language.
- Ruby manages complex information, making it easier to develop applications with less code.
Learn more about the cybersecurity programming languages cyber engineers need experience with.
Networking:
This includes routing protocols, subnetting, Voice over IP(VoIP), DNS, encryption techniques and technologies, Virtual Private Networks (VPN), and secure network architectures. You also need to know about network security technologies like firewalls and encryption.
Database platforms:
Cybersecurity concerns itself with the protection of data. Therefore cyber engineers need extensive knowledge about how data is structured, stored, and disseminated will surely help in that task.
Knowledge of operating systems:
Software systems typically run on operating systems, with each having its own vulnerabilities and idiosyncrasies. Familiarity with the operating systems you’re analyzing is crucial for diagnosing the problem.
Soft Skills Cybersecurity Engineers Need
In addition to the hard skills mentioned above, a security engineer needs soft skills to carry out the job well. The major ones the engineer needs are:
Communication skills
Security engineers often need to explain complex ideas simply. Their audiences are often laymen who have no experience or knowledge of the cybersecurity field. Though analysts are more likely to liaise with other departments, engineers are sometimes tasked with interdepartmental comms.
Problem-solving skills
Ingenuity in the response of the security engineer to breaches and attacks are an advantage.
Learning capacity
Cybersecurity engineers often read up on trends and vulnerabilities so they can quickly adapt and apply those skills against new threats.
While hard skills are vital, employers hire cybersecurity engineers that showcase both hard and soft skills. These soft skills are referred to as risk-mitigating factors, making them essential for any security engineer.
Cybersecurity certifications
Cybersecurity certifications are a great way to demonstrate that you have the skills to do a job (more on that later). Here are a few common certifications entry-level Cybersecurity Engineers may want to consider:
Security+
Offered by CompTIA (one of the most reputable tech certifiers), the certificate confirms the following: knowledge in attacks, threats, and vulnerabilities; architecture and design; implementation; operation and incident response; and governance, risk, and compliance. The certificate is universally recognized. More information about Sec+ can be found here.
Certified Information System Security Professional (CISSP):
This certification is offered by ISC2 and is considered by many to be one of the foremost cybersecurity certifications. The ISC2 has a wide variety of certifications for different concentrations. Their site offers information on who the certifications are best suited for and how you can benefit from them.
CompTIA Advanced Security Practitioner (CASP+):
This is another certification by CompTIA. To pass the certification exam, you must understand Risk Management, Enterprise Security Architecture & Operations, enterprise security integration, research, development, and cooperation. See more details on their website.
Learning Paths To Become A Cybersecurity Engineer
Before you can test for the above certifications, however, you’ve got to acquire the required skills. The 3 paths we’ve detailed below can all get you there, with varying levels of cost and time required.
Each of these paths has its advantages and pitfalls. Before you embark on your journey, take some time to understand your goals and future ambitions. That way you can select the one that uniquely suits your situation.
Do you Need A College Degree To Be A Cybersecurity Engineer?
Not necessarily! More and more often, entry-level Cybersecurity Engineer roles do not require a college degree and instead put an emphasis on real-world skills and Certifications.
That being said, here are 3 paths you could take to acquire those skills and become a cybersecurity engineer:
Path 1: The college path (4 years)
This path is the most traditional way to become a cybersecurity engineer. It involves enrolling yourself in a college and studying computer science or a related like computer engineering. These degrees tend to take 2–4 years, depending on your concentration, and can often be expensive. That said, this is the most comprehensive path, giving you the most philosophical background in cybersecurity, though they often are light on real-world applications and experience.
Pros
- Structured learning experience
- Accountability built-in
- Networking opportunities
Cons
- Can be extremely expensive
- Significant time commitment
- Skills learned can be outdated upon graduation
- Heavy emphasis on philosophy
- Few real-world practice opportunities
Path 2: Self-teaching (time varies)
These days, you can learn virtually anything online, and cybersecurity is no different. The internet offers myriad opportunities to learn and develop. This fact, combined with the high cost of college, has driven more and more people to take the self-learning route.
Pros
- Cheaper than the other alternatives
- Self-paced learning
Cons
- Requires a lot of self-discipline
- No support for hard problems
- No accountability for progress
- Can quickly get stuck and plateau
- May not learn comprehensive skills
Path 3: The bootcamp path (15 weeks – several months)
This path is designed for those who want to get into Cybersecurity quickly and without breaking the bank. Depending on the program, a bootcamp can take you anywhere from a few weeks to several months, far quicker than the traditional 4-year degree. Programs typically offer a variety of paces (full-time vs. part-time) and formats (online vs. in-person) and teach real-world, in-demand skills that employers want.
Pros
- Accelerated learning pace
- Less expensive than the college route
- Focuses on in-demand skillsets
- Networking opportunities with other students
- Built-in accountability
- Supported learning journey
Cons
- Time commitment for completing assignments
- Up-front investment (though still less expensive than university)
Get Started With Flatiron School
Flatiron School’s Cybersecurity Bootcamp incorporates the latest emerging technologies, including artificial intelligence (AI) tools in its curriculum to ensure our students are learning the most in-demand skills. During class, we have a hands-on, community approach to learning, one that includes lab work, creating a real-world portfolio, and 1-on-1 instructor access.
Ready to start walking the path to becoming a Cybersecurity Engineer? Apply Today!
If you need time, test-run what we teach in the course with our free Cybersecurity Prep – no strings attached!




