Cybersecurity is more in demand than ever before. Between the numerous cyber attacks occurring in 2024 and the huge demand for cybersecurity positions, ranging from cybersecurity analysts to threat analysts projected to grow around 33% over the next ten years, cybersecurity is a bigger topic now than it’s ever been. Ten years ago, many of us wouldn’t have ever even heard the phrase, let alone know what it meant.
Now, estimates suggest that there are nearly 4 million vacant cybersecurity jobs. Unsurprisingly, with so many headlines about cybersecurity, there’s also growing interest in joining the industry. So, what are the best programming languages for cybersecurity? Let’s find out.
Why learning programming is important for cybersecurity
Simply put, it makes you better at your job. Understanding programming helps cybersecurity experts examine software and discover security vulnerabilities, detect malicious codes, and execute tasks that involve analytical skills in cybersecurity.
The choice of which programming language to learn, however, isn’t so simply put.
The language to learn depends on your concentration, which could be in computer forensics, security for web applications, information security, malware analysis, or application security. Though the importance of any given language varies by role, programming experience offers a higher competitive edge for cybersecurity experts over others.
And although not all cybersecurity positions require a programming background, it’s an important skill to have for mid-level and upper-level cyber positions. A strong understanding of programming languages helps cybersecurity experts stay on top of cyber criminals, and having a good grasp of the architecture of a system means that it is easier to defend it.
Fortunately, the beginning of a cybersecurity career is the ideal time to build your programming knowledge. This way, when you hit the job market, you’ll know the essential components of programming and will be able to read code and comprehend its functions.
What programming language should I learn for cybersecurity?
There are about 250 prominent computer programming languages used today, with as many as 700 used around the world. In cyber, that number shrinks to around 10-15. Here are the twelve best programming languages to learn for cybersecurity, so you can set your sights toward starting a new cyber career.
Python
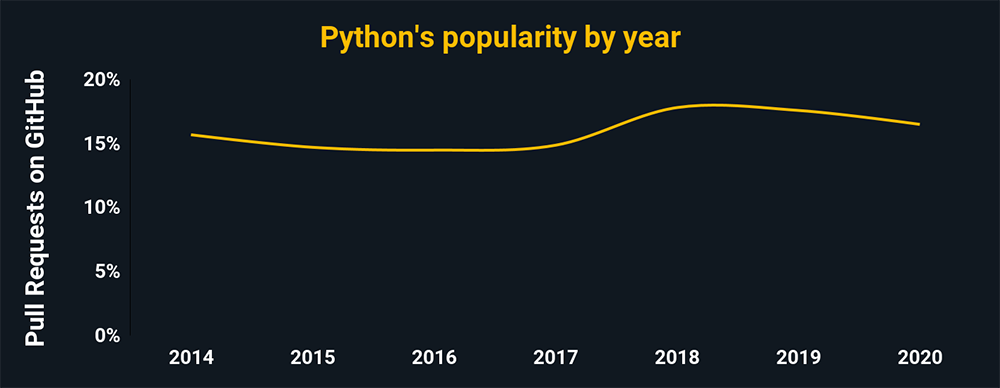
For several years now, Python has been a dominant language in cybersecurity. It is a server-side scripting language, so the resulting script doesn’t need compiling by coders. It’s a general-purpose language that is used in many — if not most — cybersecurity situation.
With Python, you’re able to automate tasks and perform malware analysis. Plus an extensive third-party library of scripts is readily accessible, meaning help is right around the corner. Code readability, clear and easy syntax, and a vast number of libraries are some of the aspects that make it popular.
For cybersecurity experts, Python is a valuable programming language since it can be used in detecting malware, penetration testing, scanning, and analyzing cyber threats. If you understand Python, being a SOC support pro makes a whole lot of sense.
You need to build tools and scripts in this role to protect web pages from security threats. To examine the root of the issues, you can also employ data, logs, and artifacts.
As a side note: The chart above shows the relative popularity based on how many GitHub pulls are made per year for that language. This chart and all the charts below are based on data from GitHut 2.0, created by littleark.
Golang
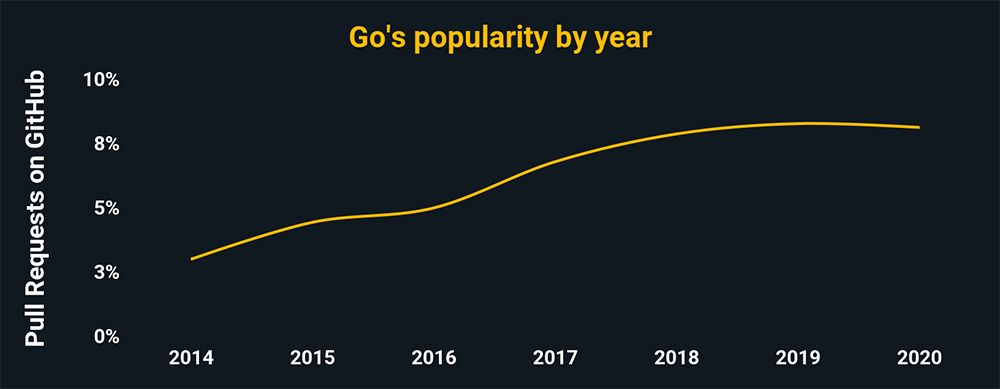
- Most malware aims to get into target systems undiscovered, making Golang perfect for it.
- With Golang, a single source code can be constructed for all major operating systems.
- The size of malware coded in GoLang is large. This helps them to penetrate systems undiscovered since large files cannot be scanned by a lot of popular antivirus software.
- This language also has vast libraries that make the malware creation process very smooth.
Go has become quite popular as a language for security professionals. It’s a perfect option for cyber programmers for its use in server and cloud services, flexibility and ease, and data analysis capabilities.
JavaScript
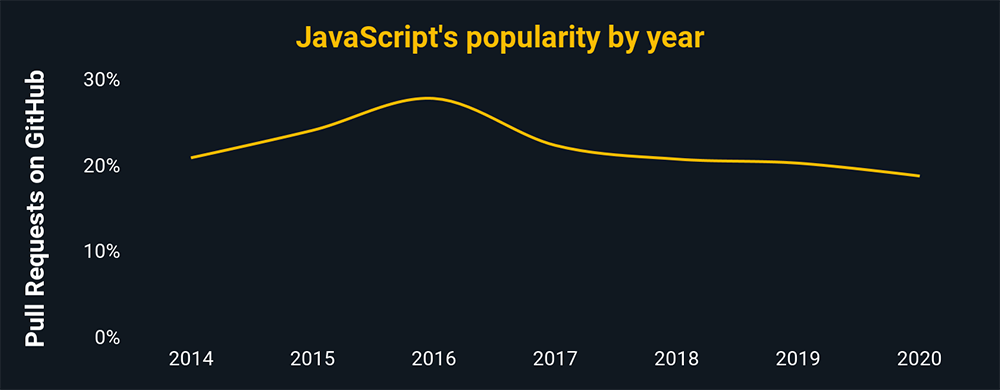
The most common programming language is JavaScript, a universal language used by 95 percent of internet sites.
It’s one of the finest programming languages for cybersecurity you can master.
- JavaScript is for you if you want to capture cookies, exploit event handlers, and carry out cross-site scripting.
- NodeJS, ReactJS, jQuery — these are all JavaScript libraries.
- This also implies that, due to the widespread use of the language, applications and systems using it are prominent targets.
JavaScript lets programmers use any code while users visit a website, strengthening that site’s functionality. On the other hand, it may produce malicious functionality hidden from the visitor. If the web site is compromised, malicious codes may be used to run a program.
If you’re a JavaScript expert, you can ensure that any site is safe enough to reduce or even remove Cross-Site Scripting (XSS) attacks.
JavaScript’s also used by front-end developers, full-stack developers, back-end developers, and more. It’s the most versatile language there is, and the most popular language there is.
C
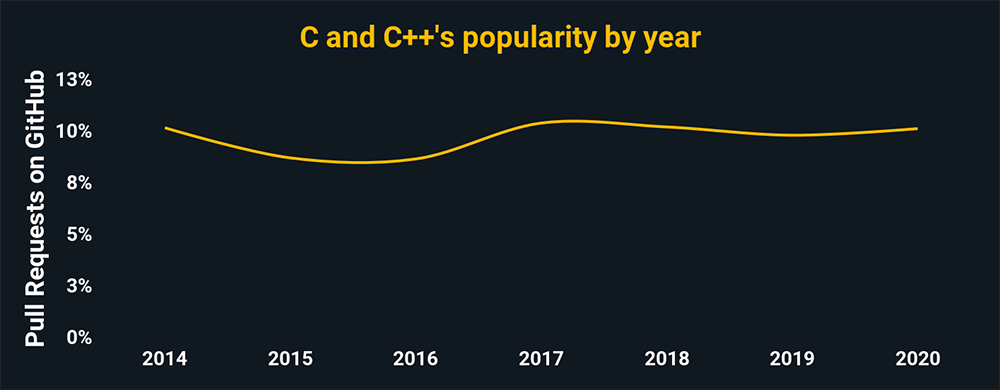
- Applying C language in reverse engineering facilitates the development of antivirus programs because cybersecurity teams can disassemble a malware to examine its design, spread, and consequences.
- The C programming language is also essential for developers who QA code integrity.
- Cyber enemies may also use the language to identify exploitable weaknesses in the network before an attack is launched.
Being a low-level programming language with simple syntax, someone can master it with a few months of training. Programmers take further steps to make sure that their code lacks bugs when writing the program. Hackers can use it to find vulnerabilities, though.
Lint is a code analysis tool intended for programs that are written in C. Different versions have emerged since its inception. Both cybersecurity experts and hackers may use Lint to identify programming errors, and find bugs that risk computer network security.
C++
C++ was adapted from the C coding language, but has several distinct features.
- In contrast to C, C++ supports objects and classes.
- C++ is faster and performs better than the C language.
- Despite being useful, less than 0.1% of all websites use it.
- A C++ developer develops desktop and mobile apps, whereas coding specialists identify and eliminate any vulnerability and bugs.
Cybersecurity experts benefit learning C++ because they can detect vulnerabilities and security weaknesses easily. A scanning tool like Flawfinder that scans C++ lets cyber experts easily recognize security flaws in code. These tools describe existing vulnerabilities, their severity, and their effects on an application by using an integrated database that includes the language function’s possible risks.
SQL
SQL (Structured Query Language) is a domain-specific programming language. It highly popular and is used to parse data in large databases. With businesses becoming more data-driven, SQL is the most demanded database management programming language.
- Most websites use SQL for their data management activities like Relational Database Management System (RDBS).
- It deals with numerous database systems.
- Consequently, it is also recognized as the most straightforward language for handling a database.
Database Administrators, programmers, and end-users create SQL queries for the retrieval, insertion, modification, and removal of data stored in database tables. Attackers often use this language to steal confidential data, compromise data stores, and execute a variety of web-based attacks.
You’ll need to have at least a basic knowledge of SQL if you want to comprehend the activity of the attacker and avoid SQL injection as well as other database-related attacks.
Assembly
- An assembly language is any low-level language that helps analyze and understand how malware works.
- Understanding assembly is relatively straightforward, especially if you already know a high-programming language.
In 2003, Slammer, a malware based on assembly, caused disorder and slowed web traffic by forcing service negligence on many, many proprietors. There was a protective overflow bug on Microsoft’s SQL server that the program exploited. This incident was not a sudden one — several months before a patch was released — but several enterprises didn’t implement it, opening the door for the bug to propagate.
Assembly is an essential programming language as cybersecurity experts might use it to interpret malware and understand their modes of attack. Cybersecurity professionals defend against traditional and contemporary malware continuously, and so it’s essential to understand how malware functions.
PowerShell
PowerShell is a more versatile command-line interface that blends the old Command Prompt (CMD) features with an advanced scripting environment that can be used to get access to the inner core of a machine, including Windows APIs access.
- PowerShell is a valuable tool to automate repetitive tasks for administrators, but sadly, its capabilities have also been exploited by malicious actors.
- No longer having to rely on typical malware, Hackers can manipulate PowerShell to find sensitive domain information and load harmful executables (also known as fileless malware).
- Because PowerShell is installed on all machines from Windows 7 to Windows Server 2019 by default, it’s a preferred tool for many attackers.
Ruby
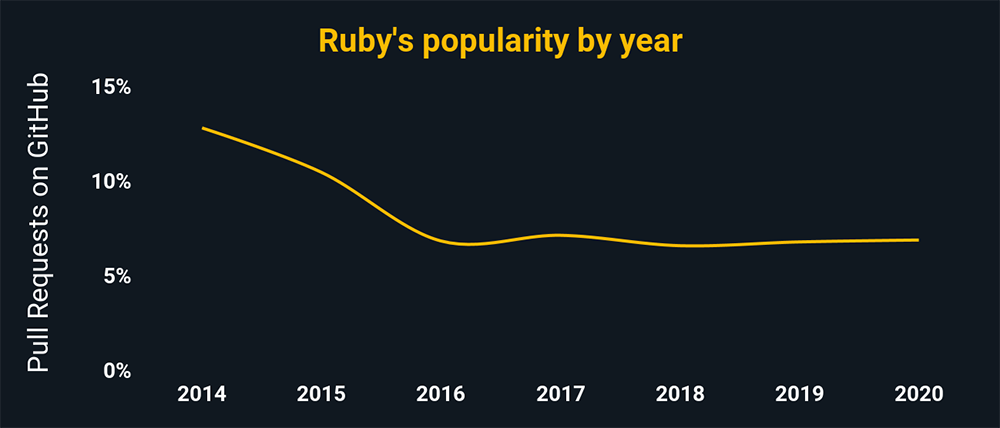
Ruby is a general-purpose high-level language created and developed by Yukihiro Matsumoto in Japan. Since then, it’s become one of the most popular programming languages in the world.
- Ruby’s syntax is essentially identical to Perl and Python.
- It was written in C.
- Its ease of use and inherent ability to manage massive code projects make it popular among coders.
- Ruby has been widely used for sites including Airbnb, Hulu, Kickstarter, and Github.
- Ruby manages much of a machine’s complex information, making programs easier to develop and with less code.
Java
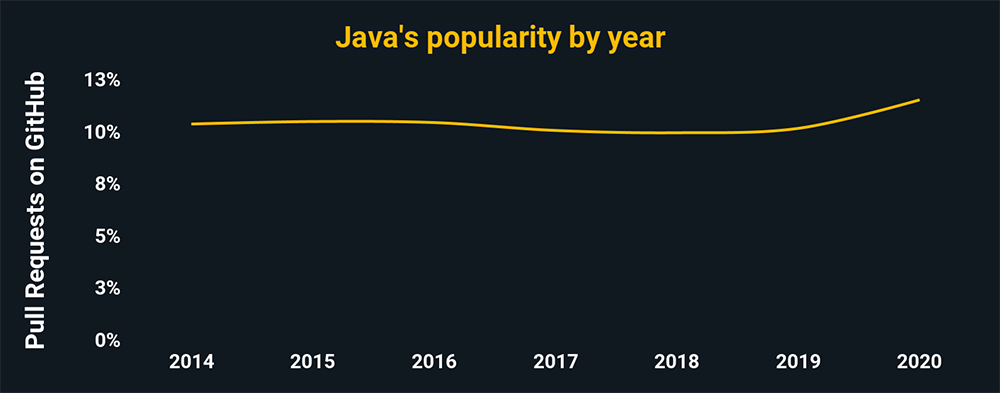
Java is one of the first languages to be used in the design of many major operating systems, like Solaris, Linux, macOS, and Microsoft Windows. Since it drives both modern and legacy web servers, it is extensively used in all industries.
In information security, the Java language has many applications.
- Cyber adversaries, for instance, use it to reverse-engineer proprietary software applications to discover and exploit security vulnerabilities.
- Penetration testers often use Java to organize high-scaling servers they use in payload delivery.
- Pen testing is one of the essential tasks of a cybersecurity specialist, and understanding Java makes it easier.
- Experienced ethical hackers use Java programming to build and develop sophisticated, ethical programs.
- Java is highly dynamic compared to languages like C++, making it popular among cyber experts.
- Using Java to develop vulnerability testing programs lets ethical hackers deploy it on multiple platforms.
PHP
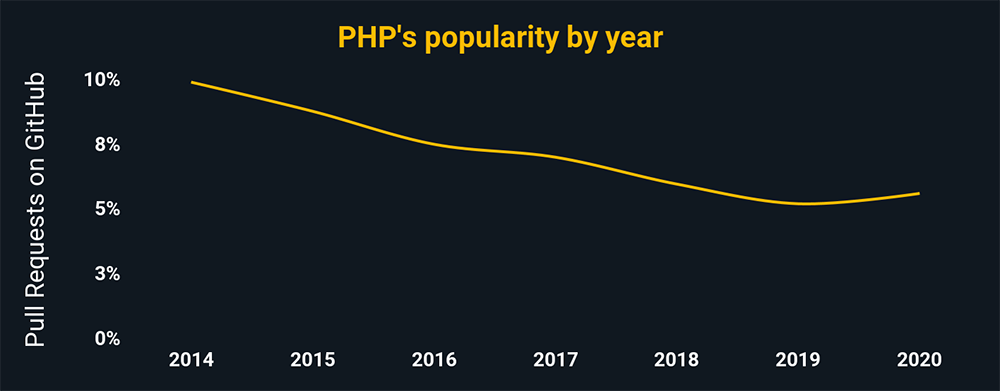
PHP is a server-side programming language used to build websites. PHP is perhaps the most powerful server-side language there is, used in 80 percent of the web’s top 10 million domains. For this reason alone, it’s obvious that understanding PHP will help you protect against attackers.
- RIPS is a standard tool for PHP applications that performs automated security analysis.
- In an application, RIPS examines data flow from input parameters to critical operations.
- You could use RIPS if you’re a PHP developer working with security vulnerabilities.
- As a PHP security-focused developer, you can write server-side web application logic.
- You can handle back-end resources and data sharing between servers and their consumers using PHP
- You can also use your PHP knowledge to eliminate any vulnerabilities in your code.
It’s also worth noting that PHP is used by businesses as a language on the server-side that works with HTML, helping websites work properly. To make website updates easier, web designers use PHP to connect databases with web pages.
Shell scripting
Shell scripting incorporates several of the same commands that you may already use in your operating system’s terminal sessions and lets developers create automated scripts for various routine activities.
Do you need to provision accounts quickly and facilitate sufficient access? Do you want to automate a system configuration security lockdown quickly? This is where shell scripting comes into play.
You’ll want to master some Linux script languages like Bash if you’re using Linux or macOS. If you’re a Windows pro, immerse yourself in PowerShell.
What’s the first cybersecurity language I should learn?
We recommend starting with Python. The syntax is straightforward and there are countless libraries that make your coding life much easier.
In cybersecurity, Python is used to conduct many cybersecurity tasks like scanning and analyzing malware. Python is a helpful step towards more sophisticated programming languages, too. It offers a high level of web readability and is used by tech’s largest companies, including Google, Reddit, and NASA. Once you have Python down-pat, you can move on to high-level programming languages.
What are the best ways to learn these cyber languages?
Like with any type of coding language, there are lots of ways to get started learning. It really all depends on how much time and money you’d like to commit to. If you want to learn casually or dabble in coding before committing, we suggest starting with a free introductory course. And if you know you’re ready to pursue a career in cybersecurity, then a full-time bootcamp is your best bet.
Introductory cybersecurity courses
Coursera’s Introduction to Cybersecurity. Built to help learning understand modern technology and strategies for information and system security.
EdX. This course provides a high-level introduction to cybersecurity and is suited for people interested in internet security.
Flatiron School’s Cybersecurity Prep Work. Learners who want to dive into cybersecurity fundamentals like virtualization functions can get started with this free prep work.
In-person cybersecurity courses designed to help you change careers
Evolve Security. Evolve Security is an interactive and hands-on cybersecurity training program for 20 weeks. Students spend roughly 20 hours a week on cybersecurity bootcamp training, including in-class and individual study.
SecureSet. This 800-hour comprehensive course is intended to help you learn the skills to become a level 1+ strategic analyst, security engineer, or penetration testing officer. SecureSet’s is a part of Flatiron.
Fullstack Academy. Fullstack Academy is designed to take you from a cybersecurity beginner to an in-demand cybersecurity expert in only 17 weeks of full-time training.
Flatiron School’s cybersecurity course. This course is intended to teach you everything you need to know to start a career as a level 1+ threat analyst, compliance analyst, security consultant, or SOC specialist.
We also offer our full-time Cybersecurity Engineering course. This course focuses more on learners with a technical background, helping them start a career as a cybersecurity engineer and joining the forefront of global technological development.
The best online cybersecurity courses to change your career
Brainstation. Through this cybersecurity course, you can gain a better understanding of the technologies developed every day and how security attacks leverage vulnerabilities and evolve within cybersecurity.
Level Effect. This course focuses on security and is paired with practical applications and use cases. Develop the skills needed to secure cybersecurity job roles or advance your career with new strategies, techniques, and processes.
Flatiron School’s online cybersecurity course. Through this online program, you can gain cybersecurity Analytics skills while being part of a vibrant, buzzing group of students and tech entrepreneurs through Slack, Zoom, and in-person with nearby learners.
What other skills do you need for a cybersecurity career?
Specops Software examined 843 cybersecurity job listings on the recruiting website, indeed, to classify the essential soft skills for cybersecurity positions in the job market and which programming languages and certifications are most valuable.
Soft skills you need
- Technical ability and mindset are by far the most important skills to have
- Second is responsibility
- And third is clear written communication
Languages
- As far as languages go, Python is the most in-demand
- C++ is second
- And C is third
Certifications
- System Security Professional certification, or CISSP, is the most in-demand professional certification
- The second most crucial professional certification is the Certified Information Security Manager certification (CISM)
- CISA certification is the third most sought-after professional qualification for cybersecurity positions.
Keep in mind: each language has its own objective and serves it accordingly. The more languages you know, the better it looks on your resume and the further ahead you are than the rest of the pack.
Although many entry-level cybersecurity roles don’t require programming knowledge, programming is a key skill for mid-level and upper-level cybersecurity roles. You can succeed in your profession and move towards long-term success in the industry with a certain knowledge of at least one programming language.
If you’re seriously considering a career in cyber, Flatiron offers our flagship Cybersecurity Analytics and Cybersecurity Engineering courses to help you get there. We also offer our Cybersecurity Analytics course online, which uses the same curriculum as the in-person course.
To learn more about which one is right for you, learn more from our Head of Cyber, Dr. Jim Borders, below.
Source: The charts above show the relative popularity based on how many GitHub pulls are made per year for that language. They use data from GitHut 2.0, created by littleark.
Disclaimer: The information in this blog is current as of 2 February 2021. For updated information visit https://flatironschool.com/.



