What is cybersecurity, and why is it important?
Cybersecurity is a field devoted to the protection of computer systems, data, and information networks. The dangers to these systems are vast, and include:
- Physical dangers to hardware, like a region’s electricity grid
- Attempts to stop operations of these systems (for example, a denial-of-service attack that makes servers inaccessible)
- Unauthorized access/intrusion into systems to commit spying, the theft of intellectual property, or hold data ransom
- Repurposing systems from their intended use, like turning a baby monitor into a spy cam or using unsuspecting victims’ personal computers to mine cryptocurrencies
Cyber attacks are a risk to anyone who uses a computer, smart device, and/or the internet. The cybersecurity firm Lumu reports that 69% of North American companies reported being affected by ransomware in 2020.
Likewise, the United States suffered a major state-sponsored cyberattack in 2020 that impacted at least 2 branches of the federal government, 4 states, and many major firms including Microsoft, Equifax, and Cisco Systems.
And with Cybersecurity Ventures predicting that the financial impacts of cybercrime will rise to $10.5 trillion in 20205 (from $6 trillion in 2021), the stakes will continue to grow as companies seek to develop sound security strategies.
Key Takeaways
- Cybersecurity is a fast-growing career that touches all industries.
- Solid programming skills are a requirement across the field.
- Key soft skills are a great way to stand out from the pack.
- Certifications and networking will be critical to your career trajectory.
- High-paying jobs are available across all disciplines of the field.
Is cybersecurity a smart career?
Cybersecurity is a fast-growing career option for almost anyone, regardless of your experience. The reason? Cybersecurity roles are needed at ‘every rung on the ladder’ to ensure that there is holistic coverage of potential vulnerabilities and cyber threats.
Worldwide spending on cybersecurity is going to reach $133.7 billion in 2022. (Gartner)
Think of all the personal data people have about you. Your doctor and pharmacist. Your bank and credit card companies. Your social media companies. Your phone provider. Not to mention all the work data you’ve transmitted on your home’s internet network during the pandemic (It’s no wonder cloud security is a bigger topic than ever).
We live in a data-driven society. Data privacy concerns dominate headlines, throwing one company after the next into real reputation risk. What drives these cyber criminals? Money, unsurprisingly. Verizon noted in their Verizon Data Breach Investigations Report that 86% of data breaches are financially motivated.
And that means the market for company and consumer data will only become more competitive. Cybersecurity engineers, cyber threat analysts, pen testers, compliance analysts… careers dedicated to fighting this cybercrime are rising and rising.
What are the hard technical cybersecurity skills you need to know?
So, what is it that cybersecurity professionals do? In this section, we’ll take a look at some of the technical tasks and methods that can be a core focus for professionals in the field.
Intrusion detection
In 2019, DataProt reported that 88% of professional hackers can infiltrate an organization within 12 hours. Companies require round-the-clock monitoring to try and catch bad actors before they do damage to vital systems or steal data. Intrusion detection is often the second line of defense (after prevention) to mitigate the threat of cyberattacks.
Penetration testing
So how to prevent intrusions? Start with penetration testing (commonly called a ‘pen test’). Authorized hackers conduct simulated attacks to try and determine vulnerabilities that could be exploited by real hackers. These ‘ethical hackers’ or ‘white hat hackers’ can even employ ‘phishing’ attempts against real employees to determine if they are susceptible to such attacks.
Malware analysis, mitigation, and reversing
Malware can be especially damaging because it is easy to make and customize, and is designed to avoid detection while doing its damage. Cybersecurity analysts need to respond quickly to malware attacks, assessing and reversing damage in real-time to maintain business continuity.
Risk analysts and security analysts
The risk management space is growing, and risk analysts help paint the broad picture of real and hypothetical areas of concern. Security analysts, meanwhile, focus on taking the current available set of tools and technologies while building innovative security solutions to mitigate risks. Many of the top skills in cybersecurity fall into the broad category of security analysis, making it a key area of growth.
Does cybersecurity require programming?
Yes. Cybersecurity requires programming. Even managers need to understand the highly complex technological underpinnings of computer systems and networks. The good news? Cybersecurity focuses on some of the most common and important programming languages in the field today, and the skills you learn in these languages will be portable far only cyber.
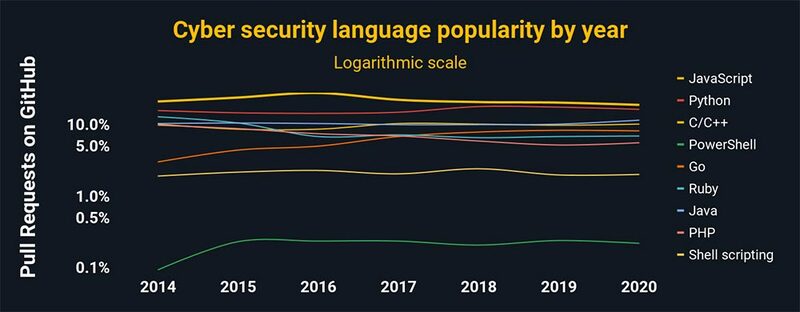
These are the most popular coding languages you need for cybersecurity:
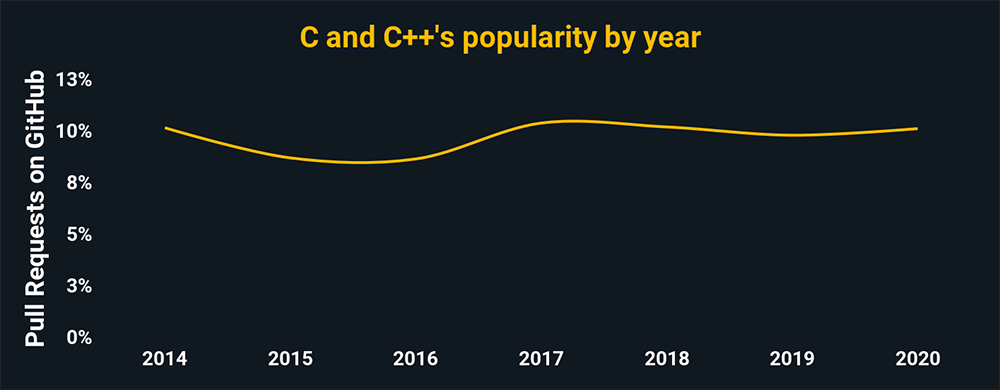
C and C++
These languages make up the core of most operating systems and applications today, making them the foundation for any cybersecurity career. Their capabilities in low-level processes and infrastructure that are key areas of hacker attention.
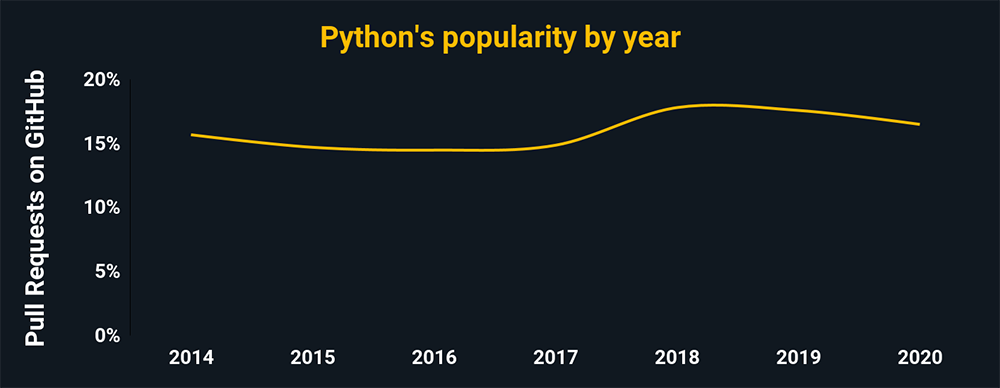
Python
Python is a high-level programming language. It will open your skillset to better automation and analysis while providing access to one of the largest libraries of third-party scripts available. It is another must-have.
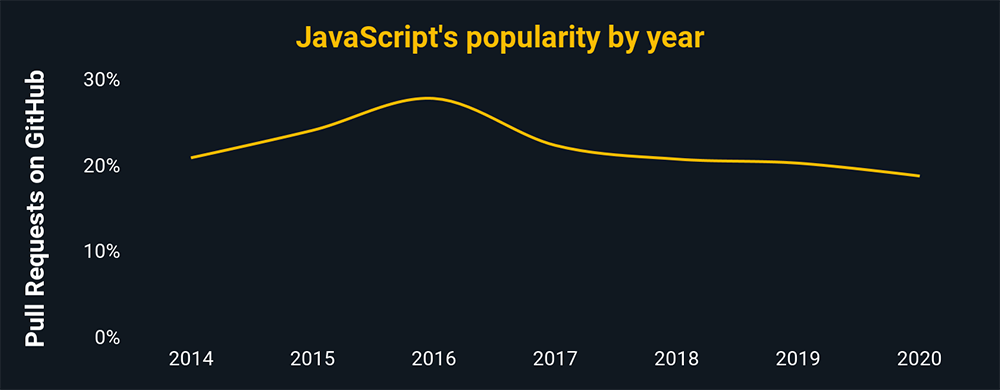
JavaScript
Web-based cybersecurity brings its own set of problems (i.e. codes that execute when you visit a website). JavaScript’s broad popularity — it’s the most popular language in the world and critical to software development — makes it a critical language for understanding cyber threats to an organization’s web-based data, customers, and reputation.
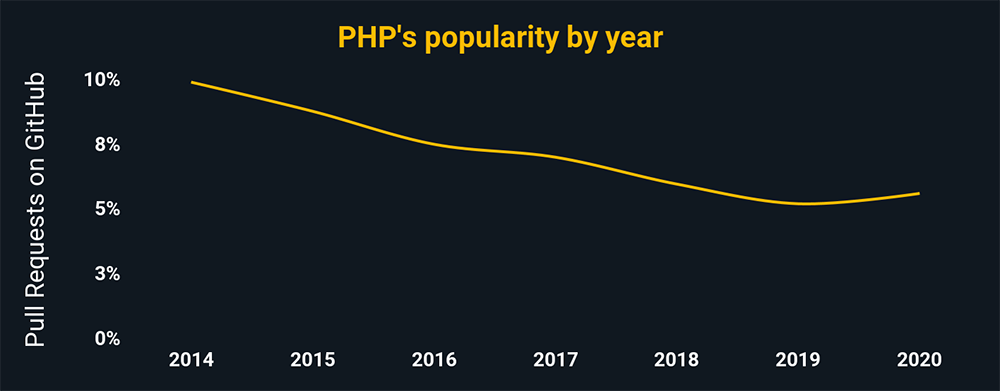
PHP
Nearly 4 out of 5 websites use PHP as their server-side programming language. Any cybersecurity career involving the web will involve PHP, especially if you’re combatting intrusion and redirect attempts, denial-of-service attacks, etc.
GoLang
GoLang is the common term for the language ‘Go’. It made headlines in 2019 as one of the top 2 languages used by hackers (along with Python). Its memory management capabilities and similarity to C have made it especially popular in the cryptography space.
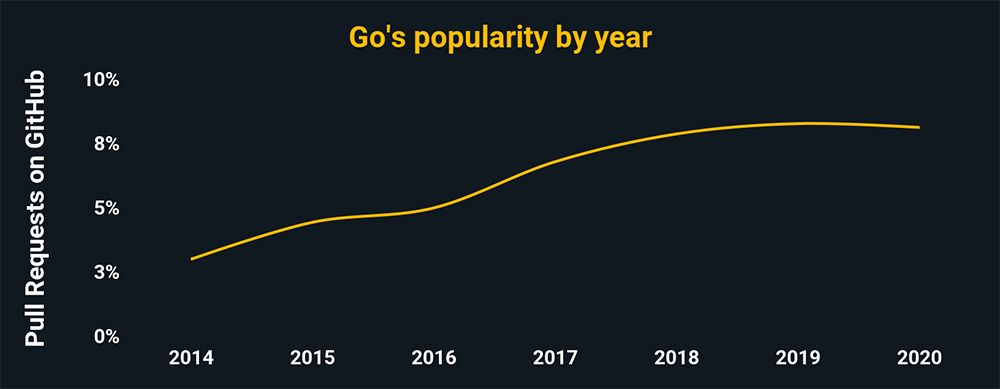
Powershell
Microsoft’s task automation and configuration management framework. The same level of power, access, and automation that makes it so valuable to system administrators makes it a prime target for hackers.
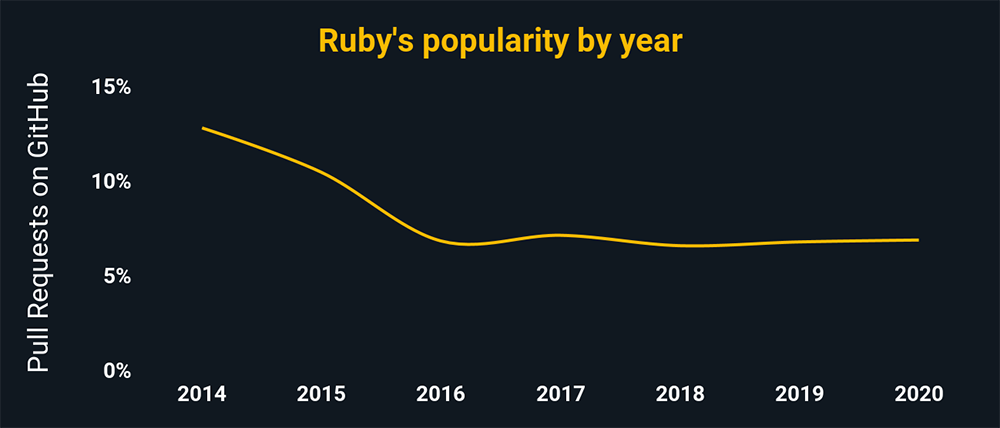
Ruby
A must-have for the penetration-testing field, given its use in Metasploit – and its broad web adoption as well.
SQL
Structured Query Language’s (SQL) widespread use in databases makes it a target for intrusion and theft attempts. A common attack is an ‘SQL injection’, where hackers will try and corrupt, steal, or modify data for malicious purposes.
Assembly
The Assembly language is the human-readable version of machine code – the low-level language that directly controls a CPU. This makes it the language of choice for reverse engineering hackers who seek to rebuild programs for competitive intelligence or piracy, or learn how to better hack/compromise them.
What are the soft skills you need in cybersecurity?
Strong soft skills like communication are critical in cybersecurity. Hackers and programmers have a certain image, and you’ll want to combat this image and focus on developing your soft skills every bit as much as your hard technical skills. This will help your day-to-day coworker relationships, and be crucial for any future interest in management.
These are the most important soft skills you need in cybersecurity:
Customer mindset
The ability to understand what a customer wants — and to get them a satisfactory solution — is fundamental to any career. Whether the ‘customer’ is your company’s client or an internal team that requires your help with a project, you’ll stand out if you carry a ‘client service’ mentality.
Communication skills
Good communication is practically a superpower in the modern business climate. And, needless to say, this goes beyond just writing and speaking well. Show that you can actively listen and correctly interpret people’s points and you’ll find your work and relationships benefit as a result. And don’t forget a key part of communication: setting expectations correctly based on your time management, deadlines, and resource needs.
Problem-solving
So much of programming is problem-solving, and it’s critical to bring that skill to other challenges. Implement logical processes and techniques and everyone will come to value your input on their projects.
Curiosity
Programmers often struggle because they don’t understand their industry as well as their business leaders do. Likewise, new programming languages, apps, and challenges present an active need for continuing education. Intellectual curiosity will help you ensure that your hard-earned skills don’t fall out of date.
Further reading: 16 Soft Skills You Need to Succeed in Cybersecurity
Information security analyst jobs will grow 31% by 2029 — 8x faster than other jobs (BLS)
Cybersecurity job outlook and salary
It’s never too early to begin reviewing job descriptions in the cybersecurity space. This will help you ensure your plan includes the necessary skills to find employment, and may introduce you to areas of cybersecurity you didn’t even know existed!
Penetration Tester
Penetration testers have one core focus: breaching the network security of a company. They employ the latest creative techniques and technologies to find weak spots before the bad guys do, and their reward is a lucrative industry salary. Further reading: How to Become a Pen Tester
ZipRecruiter Average Salary: $116,000
Compliance Analyst
Compliance analysts conduct audits, investigate incidents where controls weren’t met, and evaluate the effectiveness of policies on real-life operations. This focus on quality assurance can make it the perfect path for detail-oriented people. Further reading: How to Become a Compliance Analyst
ZipRecruiter Average Salary: $119,000
Cybersecurity Engineer
A central role on any cybersecurity team. These cybersecurity engineers need to have a total view from identifying threats to implementing complex systems and procedures to stop them.
ZipRecruiter Average Salary: $120,000
Further reading: Cybersecurity Jobs Guide
How do I become a cybersecurity professional?
Step 1: Choose your path
Do your research and pick a few similar jobs that sound like they fit your interests. Don’t feel like you need to have a bachelor’s degree in a related topic. If you are willing to put in the time and work required, a bootcamp might be just the option for you.
Step 2: Pick the right learning option
Once you know your general path, the next step is to buckle down and build the foundation of learning for your career plan. Bootcamps are a great way to learn because they offer:
- A focused, structured approach. For the length of your bootcamp, your primary focus will be to live and breathe cybersecurity in a hands-on environment.
- The investment incentive. Bootcamp tuition is a serious financial commitment in your career – and one you’ll be driven to ensure pays off.
- Small class sizes and strong networking opportunities. Bootcamps tend to provide a great student-to-teacher ratio, ensuring that you get personal attention and get to know your classmates. They often have connections to local companies seeking to hire based on the quality of previous talent.
What cybersecurity bootcamps provide the best skill set for cybersecurity jobs?
Here are just a few of the bootcamps worth checking out for your cybersecurity career move:
SecureSet (Colorado)
With three locations in Colorado, this school offers multiple programs in the cybersecurity space
Flatiron School’s Cybersecurity Engineering
Already have a technical background? This 15-week intensive program focuses on deep elements of detecting and defending against cybercriminals.
Step 3: Get your certification
Online certifications provide independent confirmations of your abilities. We typically recommend you start with the CompTIA Security+ global certification. It’s widely recognized and will help you start your career. Once you have that new experience, you can pursue a more specific path and certification.
Other popular cybersecurity certifications
As you progress in your career, you will find that there are more certifications, each focused around specific cyber disciplines. Three of the most sought-after include:
- Certified Information Systems Security Professional (CISSP), which validates your ability to design, implement, and oversee top-quality cybersecurity programs.
- Certified Information Security Manager (CISM), which positions you to think in terms of program development, management, and security governance; and
- Certified Information Systems Auditor (CISA), which focuses on assessing, auditing, and monitoring information systems.
Step 4: Build your network and conduct an efficient job search
Success in every industry requires you to focus on building and maintaining a network that you can leverage in your job search. Cybersecurity careers are no different.
Make the most of your peer and leader connections at work and use LinkedIn to stay in touch with current and former coworkers. Make sure they know about your decision to pursue cybersecurity as a career.
Likewise, consider joining one or more associations that cater to your line of work. The Information Systems Security Association (ISSA) is a major global not-for-profit organization dedicated to providing education, publications, and networking for cybersecurity professionals.
Few well-paying industries have such a high demand for talent and a relatively low barrier to entry. Now is the perfect time to consider if you want to redirect or augment your career with a move towards this fast-growing industry. Regardless of your industry, it will deepen your understanding of operations and open you up to an entire new world of opportunities.
Disclaimer: The information in this blog is current as of 19 February 2021. For updated information visit https://flatironschool.com/.




