The following is a guest post by Joe Giralt and originally appeared on his blog. Joe is currently a student at The Flatiron School. You can follow him on Twitter here.
So you don’t trust the government and you want privacy.
Assume the NSA pays 0.01cents per GB a month (which is 10 times cheaper than amazon) with a 20 million dollar budget and 114million house holds that leaves the NSA with 1.46gb per house hold. That’s a sizable sum, but not enough to hold any voice data. It’s probably just transactional data and keywords.
That would also mean that the NSA only has roughly $0.17 to spend on surveillance per American via this Prism program. Also take into consideration this blows the entire budget on storage and save nothing for data mining or the upkeep of systems.
This tells me one of two things; our information is very unsecure or they are lying about their numbers.
There’s a few things we can do to beef up our security and one of them is using TOR.
How to disappear completely.
What is TOR?
TOR was originally designed, implemented, and deployed as a third-generation onion routing project of the U.S. Naval Research Laboratory. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Today, it is used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others.
Using TOR protects you from a form of internet snooping called “traffic analysis”. TOR helps reduce the risks of both simple and sophisticated traffic analysis by distributing your encrypted communications over several proxys of the internet so not one single proxy can link you to your destination.
Tor can’t solve all anonymity problems. It focuses only on protecting the transport of data. You need to use protocol-specific support software if you don’t want the sites you visit to see your identifying information. For example, you can use Torbutton while browsing the web to withhold some information about your computer’s configuration.
Installing TOR for Mac with homebrew
IF you don’t have homebrew installed (shame on you) open a terminal window and input the following
Type : ruby -e “$(curl -fsSkL raw.github.com/mxcl/homebrew/go)
STEP 1 : Getting TOR
Type : brew install tor
STEP 2 : Get the TOR browser
https://www.torproject.org/dist/torbrowser/osx/TorBrowser-2.3.25-8-osx-x86_64-en-US.zip
TOR won’t work on all websites but it’s a start.
SO now that you are decently protected from “traffic analysis” what about your phone?
Buy an Untraceable Phone!
Get a burner phone. Unlimited talk and text for 30 days. You can even buy it with Bitcoin
Anonymous Internet Banking
How to get a debit card that doesn’t have your name it that you can use anywhere that is connected to an IBAN bank number to deposit funds into.
http://2ue35wfkmo3dlgjm.onion/
In conclusion, No ones secrets are safe. Not even the governments. If the Americas state-of-the-art spy agency can’t keep its secrets secret what hope do you have?
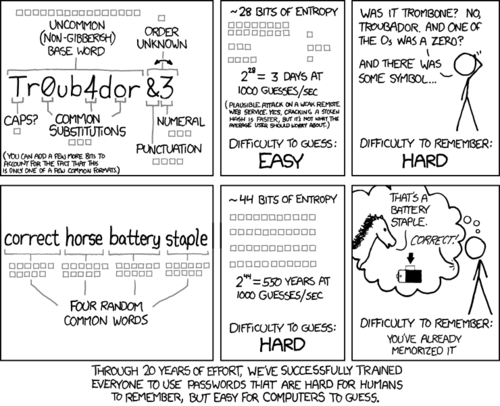
Oh and if your password looks like this… you’d should probably change it.