How to Become a Penetration Tester

Penetration testers make their living trying to break things, probe networks, and find vulnerabilities. Here’s what you need to know to become one.
Did you know that banks will pay you to rob them?
We’re not suggesting that you grab your ski mask and try your luck at your local branch, because you’ll only be paid in the form of a jail cell.
Instead, banks hire individuals to break their systems to find weaknesses so that they can secure them.
Although many classic films have dramatized robbery, vulnerability assessment (red) teams are a workplace reality. In cybersecurity, a red team is hired by an organization to break or bypass its security network.
This is where Security Penetration Testers come in. These are ethical hackers who can think and act like a criminal. But, they are trusted to document the security vulnerabilities they find (and not steal anything in the process). Every day they work with full SOC teams of compliance analysts, cyber threat analysts, and security consultants.
So, let’s get into it — how do you become a penetration tester? We’ll cover what penetration testers do, the cyber languages they need to know, salaries and job demand, how they fit into organizations, and how you can get started becoming one.
What does a Penetration Tester do?
Penetration testers are security professionals who make their living trying to break things. They are hired to probe computer networks and discover vulnerabilities that a truly malicious hacker could exploit. An organization will hire a penetration tester to emulate an advanced threat actor. They allow them to simulate a cyber attack and attempt to breach their networks and information systems.
The insights from a penetration tester’s report allow organizations to fill those security holes. Penetration testers are an essential tool for mitigating future cyber attacks, safeguarding information security, and preventing an organization from facing serious asset losses.
Penetration testers typically operate in five phases when attempting a network breach.
Phase one. Reconnaissance — Consists of sifting through a variety of outside sources (internet searches, social engineering, etc.) to note clues that may reveal insights into how the organization’s security network operates.
Phase two. Scanning — Consists of testing a network’s perimeter defense in search for glaring weaknesses.
Phase three and four. Gaining and maintaining access — These phases involve circumventing security measures and remaining within the network long enough to complete the tasks they’ve been given. This phase tests the security team’s ability to locate, contain the threat and the penetration tester’s ability to remain elusive.
Phase five. Covering tracks — The process ends as the penetration tester attempts to leave undetected, so that if they were a real hacker, they could return for future attacks.
Skills you’ll need for breaking stuff as a penetration tester
While the level of technical aptitude that a security engineer possesses isn’t necessary to be an efficient penetration tester, the more you understand what you’re hacking, the better you can bypass its security measures.
Penetration testers are experts in several technologies and platforms. They know the computer systems they’ll target, as well as network protocols, forensics (for the covering tracks phase), and scripting languages — JavaScript and Java are the two most in demand.

Penetration testers must also harness the mindset of a malicious hacker so that they can outthink the security defense measures that are currently present in the targeted network. To be an efficient Penetration tester, you must be passionate about constantly expanding your technical knowledge in addition to having an intrinsic desire to break something that has yet to be broken.
Perhaps the most important soft skill for this role is the possession of a rock-solid moral compass — ethical hacking.
Penetration testers who are successful in their roles and career paths are often faced with the ultimate test of morality. Once they successfully breach a network, their self-control is the only thing keeping them from turning into a malicious hacker and exfiltrating assets for their own personal gain. Imagine breaking into a vault at Fort Knox and leaving without a single brick of gold.
Organizations usually set parameters for pen testing exercises. Operating outside these parameters or exfiltrating data without an organization’s consent can lead to termination of employment and can even incur legal repercussions.
Other soft skills that are advantageous for this role include creative thinking and communication skills.
Salary and Outlook
It’s cool that you get to break into networks with no repercussions, but it’s even cooler that you get paid for it. According to ZipRecruiter, the average starting salary for a security penetration tester is around $116,000 a year.
A penetration tester’s salary will vary due to previous experience, technical abilities, and the location of the job. And as you continue to expand your resume as a penetration tester, your salary can easily increase.
Cyber defense is extremely important, but in an ideal situation, an organization would rather prevent a breach than contain one. Because of the penetration tester’s ability to uncover vulnerabilities before a threat actor does, they are in high demand by organizations across all industries.
For a closer look into cybersecurity careers overall, read our Ultimate Guide to Cybersecurity Careers.
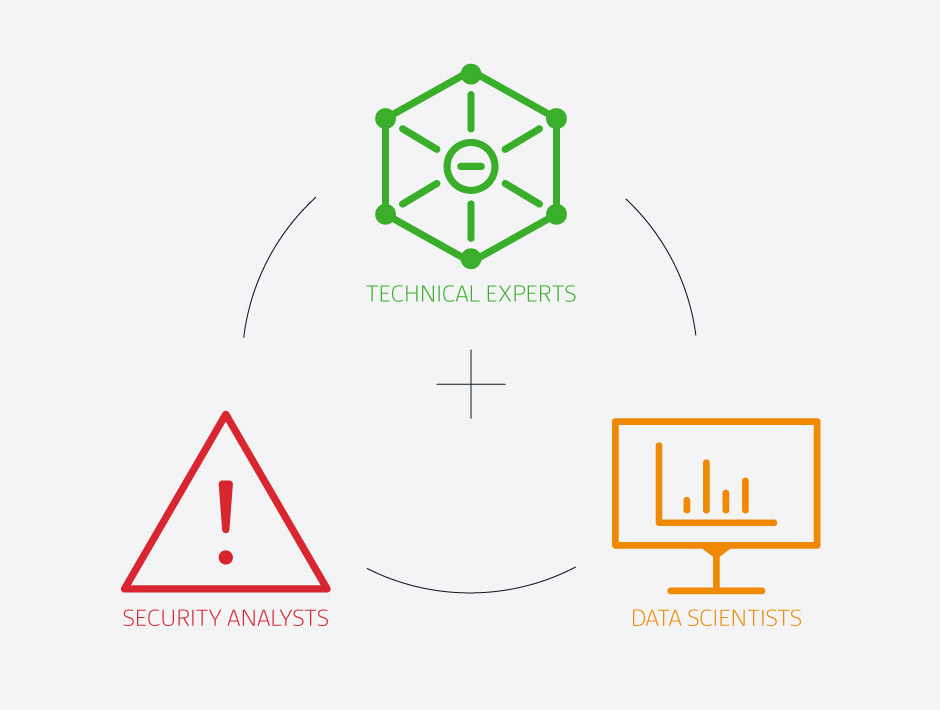
What does a security team look like?
The advancement of cyber threats has led many organizations to develop their own Security Operations Center (SOC). A SOC consists of a cohesive cyber-team made of security engineers, penetration testers, security analysts, and data scientists. Each member of the team brings a unique skill set that assists in the efforts of preventing, detecting, analyzing, and responding to security threats.
The engineers are the technical experts that build and secure the networks and the detection tools of the company.
The data scientists analyze the mass data that a company produces to discover network insights.
Analysts use these discoveries to actively search for anomalies in their network that might indicate malicious activity.
When engineers spot anomalies, analysts work to set traps and contain threats. Setting traps preemptively is “active defense.”
Penetration testers are white-hat hackers who simulate cyber attacks on their own network to discover vulnerabilities. They report their findings to the team so that, together, they can fill the network’s security gaps.
Every team member in the SOC is an essential piece of the ongoing battle against cyber threats. The question is “which team member do you want to be?”
Where does the Penetration Tester fit into the team?
A penetration tester’s report is the ultimate preemptive tool in cyber defense. If a penetration tester discovers a vulnerability, they notify security engineers to patch it up before a real bad actor exploits it.
With a security gap fixed, analysts can more easily spot a threat that attempts the same hack, thus making the defense process much easier.
In a sense, penetration testers give the SOC a clairvoyant advantage when preparing to face threat actors. Battles that may have been fought are already won because a vulnerability is no longer a viable target.
How To Get Started
No matter where you’re starting from, a Cybersecurity bootcamp can get you industry ready in as little as 15 weeks.
They are the fastest way to get the skills you need to join the cyber industry. They also prepare you for any certifications you might want on your course to your career.
Flatiron School is one of the most complete, immersive, and compressed cybersecurity programs out there. Our Cybersecurity Engineering Program teaches the technical and analytical skills needed to become an effective penetration tester. Our programs are a balance of classroom theory and hands-on lab time. This ensures that our students graduate with the level of skill and confidence needed to leave Flatiron School job-ready.
Evolve Security Academy also has a strong course that will teach you what you need.
Many, but not all, of the students who enroll in our cybersecurity program have a background in IT. But if you don’t have the same foundational skill set that doesn’t rule you out. We offer a preparatory cyber workshop that will give you an introduction to Systems, Networking, and Python.
If you’re interested in the more analytical side of cybersecurity, check out our cybersecurity analytics course.
Are you ready to break systems professionally?
The security penetration tester role puts you head-to-head with the black hats (malicious hackers). This role is incredibly unique. The temptations and moral challenges you’ll face can be just as difficult as those that are technical in nature.
At the end of the day, someone’s going to break into these security networks. But, if you do it with the right intentions, you may be directly responsible for saving an organization millions of dollars and protecting thousands of people from losing their personal information.
If you want to break things and get paid for it, then a penetration tester career could be a great fit.
Disclaimer: The information in this blog is current as of January 31, 2021. Current policies, offerings, procedures, and programs may differ.



